Up to 10 cash back SQL injection attacks. This tutorial explains how you can prevent open redirection attacks in your ASPNET MVC applications.

Frame Injection Attacks Netsparker
Hi I need help understanding the iframe injection attack and how it is performed by the hacker and furthermore how it affects different accounts on my VPS - The reason I need to know is below.

. The attacker incorporates the target website as an iframe layer overlaid on the decoy website. A successful SQL injection exploit can read sensitive data from the database modify database data InsertUpdateDelete execute administration operations on the database such as shutdown the DBMS recover the content. Clickjacking attacks use CSS to create and manipulate layers.
We start out by creating a safe and legal environment for us to perform attacks in. Search for jobs related to Web attack mass iframe injection attack removal or hire on the worlds largest freelancing marketplace with 20m jobs. E-Commerce Skimming Attacks Evolve Into iFrame Injection.
Iframe injection attack Help please. Attackers take advantage of the fact that the content of a web page is often related to a previous interaction with users. Some websites built on Joomla and WordPress have been compromised by iFrame injection attacks and are redirecting visitors to malicious sites hosting scareware and other Java-based exploits.
Go back to Tutorial. Facebook Twitter LinkedIn YouTube Articles. They are the element names surrounded by angle brackets and are of two types the start tag also known as opening tag and the end tag referred to as the closing oneBrowsers do not display these HTML tags but utilize them to grab up the content of the.
Tags iframe hack Watch tag. This type of attacks generally takes place on webpages developed using PHP or ASPNET. One of the factors that make an ongoing malware attack so difficult to stop is the speed with which the assault can evolve.
Malwarebytes didnt name which Magento-powered e-commerce site got hit by the iFrame attack although Segura says it is a clothing. By using SQL Injection attacker may know the sensitive data that is unable to read like customer private details passwords credit card bills etc. In this article.
By inserting code from web page input. The attack only affects mouse actions or similar like taps on mobile. So that when a user clicks the link they actually click the button.
SQL injection is a set of SQL commands that are placed in a URL string or in data structures in order to retrieve a response that we want from the databases that are connected with the web applications. Cross-site scripting attacks also called XSS attacks are a type of injection attack that injects malicious code into otherwise safe websites. Sql injection attack tutorial sql injection attack logs javascript injection.
An HTML tag label pieces of content such as heading paragraph form and so on. A Web application firewall can greatly help reduce the risk of. Both server-side and client-side vulnerabilities are listed in the top 3 of the OWASP top 10 Injection being the server-side vulnerability and Cross-Site Scripting XSS being the client-side vulnerability.
An attacker will use a flaw in a target web application to send some kind of malicious code most commonly client-side JavaScript to an end user. When applications fail to validate user data an attacker can. Its free to sign up and bid on jobs.
Ethical Hacking - SQL Injection. Then we cover the core concepts of SQL and injections. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application.
As per OWASP an injection vulnerability or flaw is one that encompasses SQL OS and LDAP where untrusted data is sent to an interpreter. An example using the style tag and parameters is as follows. After that we learn SQL injection techniques with the help of cheat sheets and references.
I got an email from Google saying that they added one of my sites to their list of bad ware sites the email was as follows. In this course we explore one of the biggest risks facing web applications today. Hypertext Markup Language HTML injection is a technique used to take advantage of non-validated input to modify a web page presented by a web application to its users.
All we need to attack is to position the on the evil page in such a way that the button is right over the link. This tutorial discusses the changes that have been made in the AccountController in ASPNET MVC 3 and demonstrates how you can apply these changes in your existing ASPNET MVC 10 and 2 applications. Mass iFrame injection attack now counts millions of compromised web pages.
Sarthy claims iframe injection attacks can be easily detected and fixed with online tools. Clickjacking is for clicks not for keyboard. Welcome to the Bug Bounty Hunting series where we will be learning everything we need to know so that you can begin your journey in Bug Bounty Hunt.
The recently discovered iFrame injection campaign rages on as the number of compromised web pages goes from 90000 to. Attacker may hack the web application by using SQL Injection which is used SQL database like. Thats usually doable with CSS.
SQL Injection is a type of code injecting web hacking technique. XSS Cheat Sheet Preventing XSS.

Frame Injection Attacks Netsparker

Https Sql Injection Blogspot Co Uk Iframe Injection

What Is Cross Site Scripting And How Can You Fix It

The Difference Between Cross Frame And Cross Site Scripting Daniel Miessler

What Is An Iframe Injection Mass Iframe Attack Tutorial Ethical Hacking Tutorials Learn How To Hack Hacking Tricks Penetration Testing Lab

What Is Clickjacking Tutorial Examples Web Security Academy
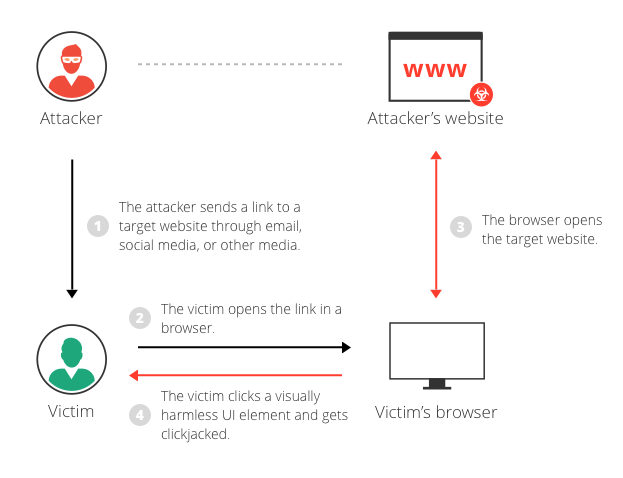
What Is Clickjacking Attack Example X Frame Options Pros Cons Imperva

0 comments
Post a Comment